Considering that SMEs have urgent demands for backup of their key application systems and a real-time backup of key data and operating system while they usually cannot afford building their own backup platform, IDC could build a backup and storage platform providing economical backup service for SMEs.
On the other hand, with businesses increasing rapidly, a manual backup will result in overwhelming workload and adds up difficulty of maintenance. Once a system failure occurs, business will be interrupted and the loss will be incalculable.
Requirements
The backup and storage platform for SMEs should support heterogeneous environment because different enterprises may use different platforms and has various types of data. It should also support custom backup strategy to better meet demands of SMEs and include disaster recovery service into the existing charging system of IDC.
Topology
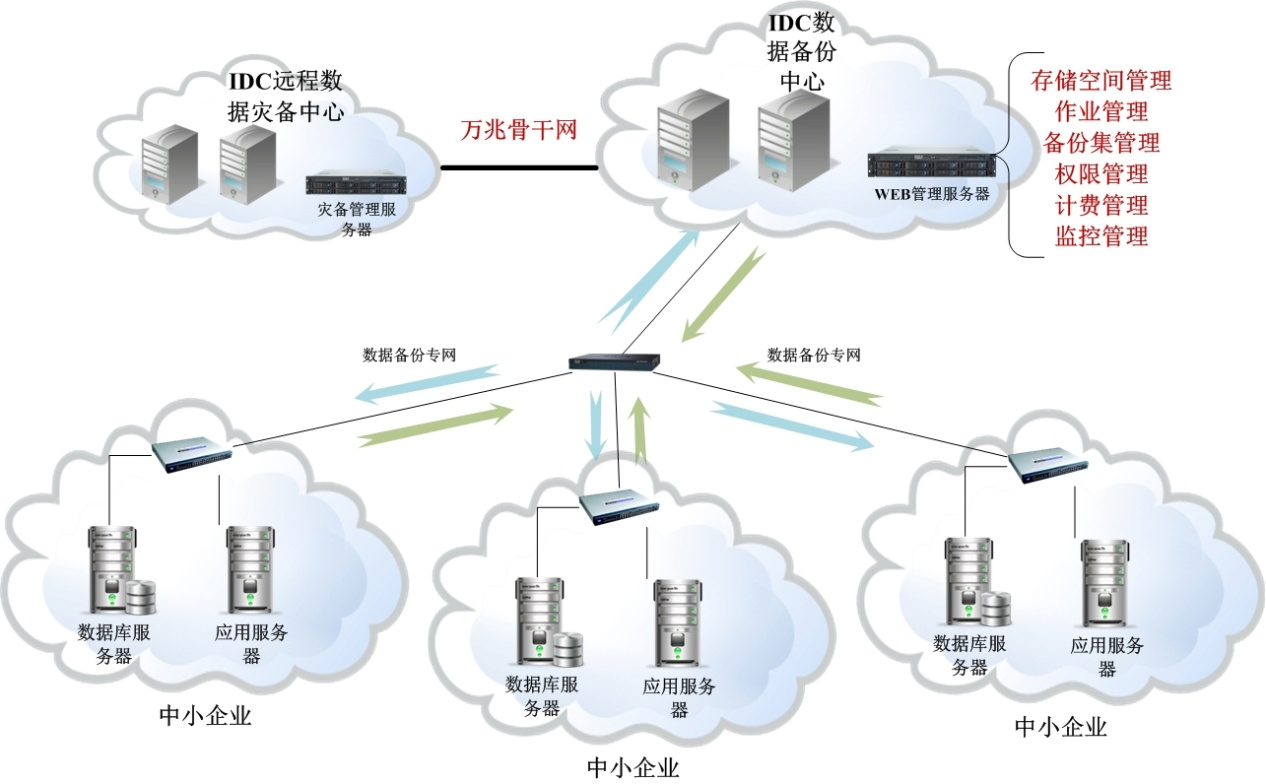
Deployment
It will apply cloud computing technology of Scutech to build a storage platform on backup server to provide backup service for customers. Users only need to install a proxy client to back up their data. Every user can easily monitor and manage their backup via an independent web page. It also applies strict access control and data encryption technology to prevent unauthorized access and ensure data security.
Advantages and characteristics
It provides comprehensive data protection for files, databases and operating systems.
Users can set up their backup strategy according to needs. The web interface provides task logs and user logs that allow users to examine operation histories, along with embedded alerting and mail notification functions that can keep users informed of backup process. A user-friendly interface allows non-professionals to easily operate the system.
It applies advanced data compression and smart bandwidth control technology to improve efficiency and reduce network traffic. It also supports resuming from broken download and data verification to ensure integrity and availability of backup data.
It does not require lots of investment at early stages and allows flexible expansion later.
]]>On one hand, e-government system can improve administrative efficiency and accelerate the transformation of government functions; it enhances governments’ ability to supervise fellow institutions and serve the public; it also promotes the development strategy of informatization driving industrialization. On the other hand, since Wenchuan earthquake in 2008, information security has become a priority; the state has introduced a series of policies and required governments to accelerate information security construction.
Requirements
Firstly, the disaster & recovery platform should be able to perform efficient backup towards heterogeneous servers (database servers, file servers, etc.) and provide a unified management terminal with ease of operation so that personnel could recover damaged data or system with minimum time and effort.
Secondly, the disaster & recovery system should enable level-to-level-management. The ministries should be able to manage provincial and municipal institutions and the provincial governments manage municipal institutions. The interface should also be aesthetically designed and easy to operate for the convenience of maintenance personnel.
Topology

Deployment
The InfoKist deployed as a backup server will be in the same network as the business server to perform unified backup and protection of files, databases and operating systems.
The InfoKist deployed as a remote disaster & recovery storage server will be placed at a different location and conduct real-time data synchronization with the backup server. In case of damages to the backup server, the remote disaster & recovery server could replace the backup server and continue to provide data backup and recovery service.
DBackup should also be installed on the file server, database server and other key application servers. Backup could immediately be conducted with simple deployment.
Remote disaster & recovery center could also be built if the condition allows. The level-to-level management function can provide multi-dimension, multi-level and distributed disaster & recovery management strategy.
With the deployments above, a unified disaster & recovery platform could be built to manage backup. It also has graphic level-to-level management interface so that personnel can maintain and manage easily. This system could reduce government expenditure, simplify the disaster & recovery framework and ensure a safe operation of e-government system.
Advantages andcharacteristics
InfoKist is an all-in-one storage server that integrates advanced hardware with Scutech’s disaster & recovery software. It significantly reduces user expense and allows unified deployment and management of the whole disaster & recovery system.
It supports various operating systems like Windows, Linux and Unix and provides unified monitoring and management of backup and recovery via WEB page.
It supports a full protection for files, databases and operating systems. Supported databases include SQL Server, Oracle, MySQL and domestic databases like DM.
It provides multi-level backup & recovery. Business system could be instantly recovered in case of a complete failure of local machine room.
It provides data transmission under limited bandwidth. Even with poor and unstable network, backup could still be completed.
It provides de-duplication technology to significantly reduce resource occupation and improve efficiency.
It provides a graphic and extendable backup management platform; every closed loop could be served as a management node after system upgrade.
]]>As electronic systems taking an increasingly important role in enterprise operation, the data volume it generates is increasing fast which has turned into an important asset of enterprises. A loss of data such as client information, product profile and project information will cause imponderable losses and influence its market status.
Requirements
Issues facing these enterprises include: a) low efficiency and lack of reliability of manual backup considering the large amount of data and complexity of enterprise structure; lack of efficient supervision as superior institutions can only examine works of fellow institutions by inquiry; no backup for the system and no business takeover to guarantee an instant recovery of business in case of downtime, etc. therefore, enterprises craves for a data backup platform that integrates backup management, disaster & recovery for the system and other functions to ensure data security.
Topology
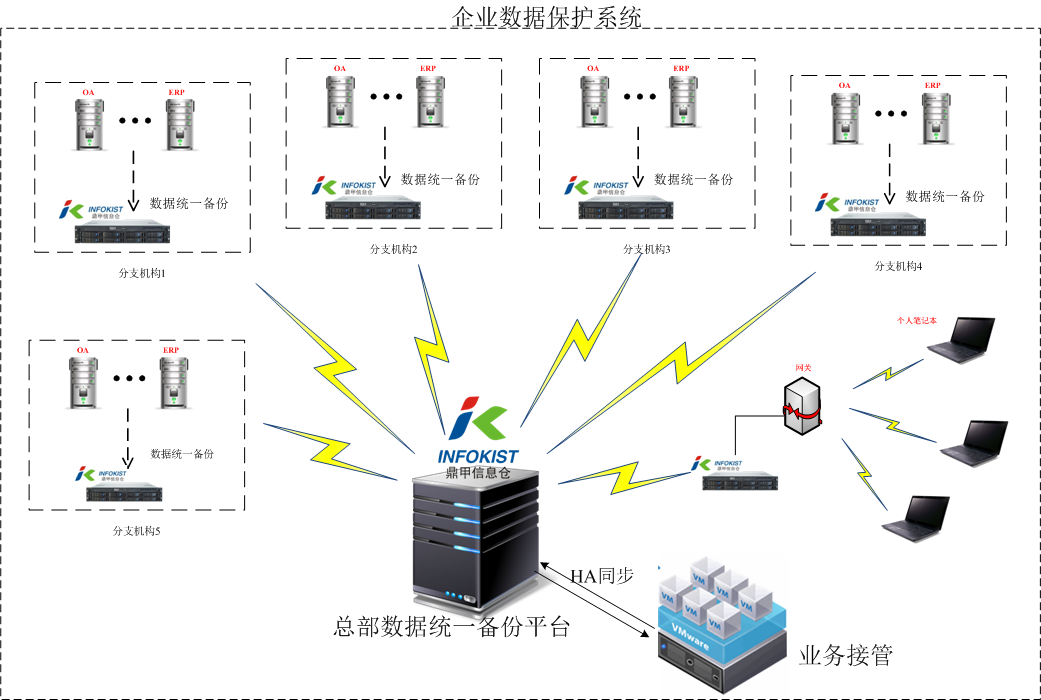
Deployment
InfoKist will deploy a unified backup platform at headquarter and subsystems at fellow departments to backup and protect the business server. Subsystems will be connected to headquarter and synchronize data to the business takeover platform which will take over the business in case of server downtime. Headquarter can perform unified monitoring and management towards all subsystems. A gateway server will also be deployed for sales personnel to connect with the internal server and backup their laptops.
Advantages and characteristics
InfoKist could perfectly meet the demands of large enterprises with multiple branches. It provides a comprehensive backup and protection for the files, databases and operating systems across multiple business platforms.
Business takeover function significantly reduces recovery time and guarantees business continuity;unified data query function eliminates delay of inquiry and reduces workload of production server.
InfoKist also bridges between nodes on account of the complexity of enterprise structure. It maximally integrates and utilizes resources and allows flexible expansion for nodes. New business systems could be added as a backup node with new authorization,
It supports flow control and Ultra Narrow Band transmission to backup and transmit big data under limited bandwidth conditions. It also supports concurrent data backup of multiple nodes. InfoKist can also resume from broken download and ensures integrity of backup data.
.
]]>As the current information system in electricity department is mainly based on OA system, electricity power examination system and production system, it will inevitably produce huge data and is potentially open to breakdowns due to heavy workload. Therefore, it is extremely important to ensure data security to prevent unaccountable loss caused by system downtime or data loss.
Requirements
Information departments of local State Grid currently back up data manually or through writing scripts, which are hard to manage, operate and maintain. Without verification of backup data, the validity can not be ensured. Besides, without an efficient backup method, a lengthy recovery during downtime will cause great inconvenience for people’s life. In order to ensure data security of local business systems and continuous operation of application systems, a disaster recovery system needs to be built that is user-friendly, highly autonomous, and extendable, meanwhile allows unified management and monitoring.
Network topology
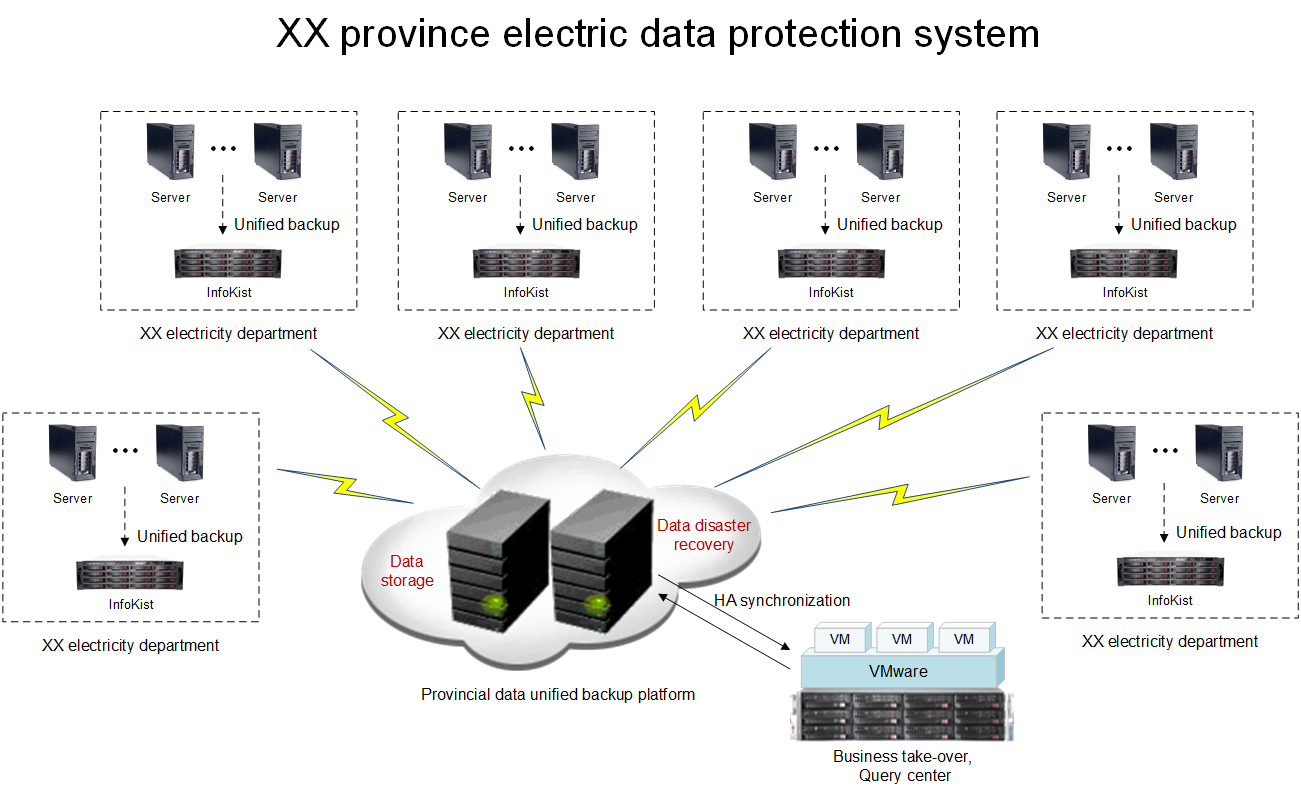
Deployment
Cities build relatively independent backup sub-servers using InfoKist which then are connected with provincial cloud backup platform through a special line to synchronize data. With off-site high availability technology of Scutech, a remote virtualization platform can be built as a business takeover disaster recovery center. Once an accident occurs, it can instantly take over the business server and maintain normal operation. In terms of management and monitoring, users only need to log onto the web interface to set up and manage clients. Municipal departments are independent from each other while provincial departments can perform unified management.
Advantages and characteristics
Multiple disaster recovery mechanisms can be built to ensure data security by building a local backup server, an off-site backup server and a remote business takeover center. Business systems can continuously provide service to customers with virtualization technology which immediately activates another platform to takeover in case one fails.
The private cloud backup platform is easy to deploy and extend which allows for a flexible distribution of resources among municipal backup centers.
The platform can also balance workload among several backup servers and optimize network transmission to reduce traffic and minimize pressure on ongoing businesses.
Also, a strict user access control and 128-bit encryption guarantees transmission security and stops users from accessing the data they are not authorized to.
]]>Data is an important asset of banks. With the rapid development of banking industry as well as the wide use of IT systems, loads of sensitive information such as accounts, client names, and transaction logs have been produced and used inmany working scenarios, like business analysis, development testing and even outsourcing businesses. A leak or damage to data of such sensitivity will cause huge loss to the bank, not to mention the influences on customer trust in the bank and the security of its information systems. In mid-2012, the most severe information leak incident in US financial sector resulted in information leak of around 40 million credit cards which directly damaged client interests. It has become vital for banks to ensure data security during business analysis, development test and auditing & regulation.
Severe data risk
According to Ponemon Institute, 84% of the companies being investigated use authentic client information during software development and testing, 70% use customer data and 51% use credit or payment information.
Surprisingly, around 45% of companies being investigated did not try to protect the authentic information being used despite its sensitivity, which means there is a huge risk of information leak when financial institutions use such data. In fact, it exists not only in financial institutions, but also medical departments, governments and enterprises. Once such risk becomes a fact, the damage is unimaginable.
Data desensitization
Data desensitization is to alter figures of data while preserve its original features to protect sensitive data from unauthorized access but is still available for processing. By data sensitization, information could still be used and connected to business, preventing data leak without breaking any laws.
Related regulations
International: Sarbanes-Oxley Act, PCI-DSS, GLBA, BASEL II, GDPR, HIPAA and other regulations targeting the leak and stealing of sensitive and personal information. These regulations require organizations limiting user access according to their positions.
Domestic: In A Draft of Regulatory Guidelines for Policy of Development of Information and Technology in the 12th Five-year Plan for Banking Industry released by CBRC (China Banking Regulatory Commission), it clearly states “to strengthen security management of data and files and gradually establish protection mechanism of information according to the type and level. To strengthen control of high-risk segments such as the storage and transmission of sensitive information, to build a strict approval mechanism for the access of data and files and to apply data desensitization for data used in testing to prevent any leak of sensitive data.” In the Guideline of Risk Management of Information and Technology released by CBRC, it states that “commercial banks should introduce clear regulations and strictly manage the collection, processing, storage, transmission, distribution, backup, recovery, cleanup and destruction of client information.” In the Guideline of On-site Risk Inspection released by CBRC, it states that “Data desensitization should be applied if production data is to be used in testing, and whether it should be approved by high-level management layer, apply certain restrictions and conduct data desensitization when production data is to be used in testing.” Under such context, data desensitization technology was developed and adopted by more enterprises in recent two years.
Requirements
Requires deployment of professional data desensitization systems and devices to build a secure and reliable data security protection system to ensure private data of enterprises and individuals being bleached and processed efficiently and prevent potential information leak.
Requires a wide range of desensitization algorithms to process sensitive information in testing environment and meanwhile to ensure validity of personal sensitive information.
Requires the data desensitization system to auto-search sensitive information (such as: name, date of birth, address, identity, phone number, bank account) according to the sensitive information categorization principles to ensure secure use of client data in non-production environment, prevent sensitive information leak,meet the requirements of auditing and regulatory departments, etc.
Network topology
Advantages and characteristics
Advantages:
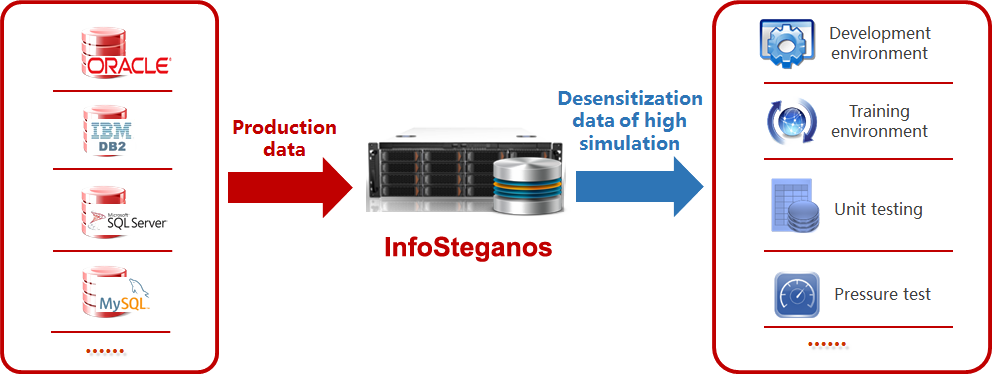
Auto-search
Firstly, users need to define private data for the application system and build a complete private data model and relation for databases.
The auto-search function will sample from production data sources, scan and analyze the samples based on built-in algorithms of InfoSteganos, and then it defines which fields are private data and what type of private data they are.
Data extraction
It periodically extracts authentic data to InfoSteganos devices according to the definition of production data stored in InfoSteganos.
Bleach and desensitization
It conducts data desensitization of acquired authentic data according to the exisiting private data model to produce forged data which are stored on InfoSteganos devices. Because the devices operate in a closed system, it prevents data leak well. The characteristics of forged data are as follows:
1. High simulation;
2. Maintains data correlation;
3. Irreversible algorithm;
4. Data uniqueness;
Data loading
Users can log onto InfoSteganos platform with limited access to acquire testing data. The platform can connect to a non-production database and writes the forged data into the target database.
1. Supports heterogeneous production system and database in testing environment;
2. Supports metadata loading;
3. Supports total and sampling loading;
4. Supports data subset loading;
5. High-speed writing in batches by default
Characteristics:
Ready to use; hardware-software all-in-one product with all parts already integrated;
A wide range of built-in desensitization models and algorithms to reduce implementation cost;
User-friendly interface with powerful functions;
]]>